Using a hard drive degausser in your business can provide total protection for your customer or employee data, but what are some of the advantages of investing in a data degausser? Below we explore some of the advantages that secure data erasure can provide businesses, not just from a practical standpoint, but also, from the point of view of the customer.
With data security becoming more prevalent and following on from the European Union’s strict GDPR law, businesses are looking for solutions whereby they can protect their customer and internal data while also complying with legislation to ensure safe data disposal.
Here are some of the advantages of hard drive degaussing and the use of magnetic data erasure in businesses today:
Data security compliance for GDPR and data law
GDPR is one of the world’s strictest data compliance laws affecting all businesses that trade with or operate in the European Union. Data security has increasingly faced scrutiny after several high profile data breaches in the past several years have made governments step up their efforts to ensure people’s personal data is protected.
Hard drive degaussing can help businesses erase data from a large number of different mediums to ensure that customer data is properly handled. This is particularly the case when systems are being upgraded and replaced with newer frameworks. The hard drive disposal process is delicate and should data not be erased from all mediums, businesses affected by the new GDPR data protection law can be held liable if data is hacked or accessed by a third party without customer consent. In this situation, disposing of hard drives requires secure data erasure through the use of a degausser so that it cannot be retrieved later.
Destroying a hard drive’s sensitive data
For many businesses holding sensitive data – being able to erase hard drives securely is a must. This is because a simple hard drive wipe with software doesn’t magnetically remove the data from the actual hard disk itself. Sensitive data, particularly if handled by security companies, the defense industry and other government departments needs to be disposed of with the highest level of erasure, and without third parties being able to recover the data.
Sensitive data erasure with degaussing is also beneficial for businesses that want to reassure investors and stakeholders that there are internal procedures for data handling and that these are being followed strictly to ensure data safety.
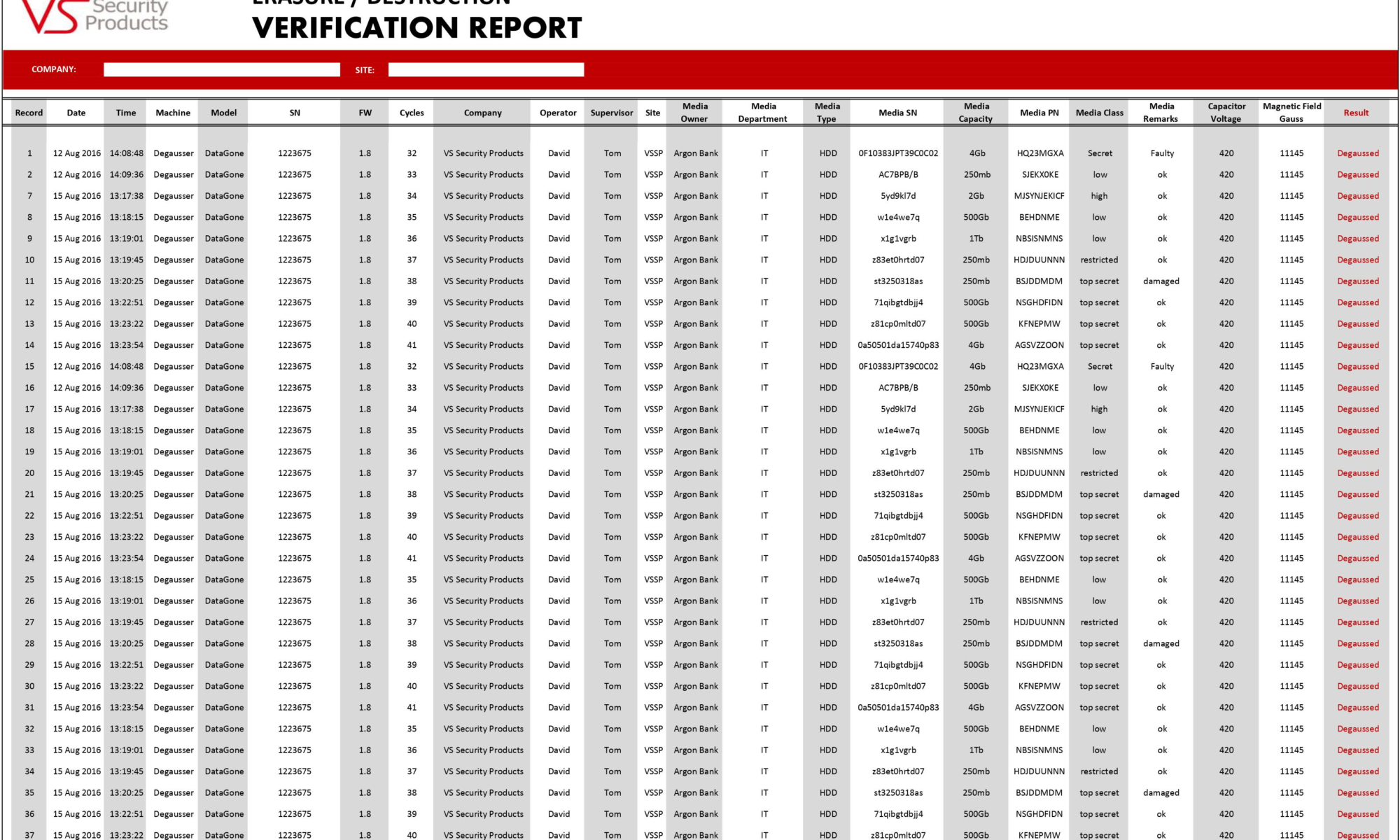
Hard drive degaussing audits for transparency
Businesses can leverage hard drive degaussing audits to demonstrate their processes for data erasure. This information can be provided to senior stakeholders in the business, managers and other C-level executives to show hard drives being erased and the full reporting of each set of disks that have successfully gone through the process. These reports can also be used elsewhere for legal investigations and for general business data security practices.
You may like to see the DataGauss XL-LG that comes with an auditing tool.
Ensuring customer data doesn’t fall into the wrong hands
Being able to erase hard disks securely through degaussing helps businesses erase customer data completely from their systems. This can then be confirmed to customers in writing and supports business transparency as well as ensuring that no third parties can access older data or break into systems to gain sensitive data.
Supporting internal data processes
Hard drive degaussers can be brought into a company and form part of the data erasure process. Businesses will already have existing processes and may wish to further strengthen their data disposal by adding a layer of security through degaussing. By investing in a hard drive degausser unit, a business can support the internal data erasure processes, create transparent reports and provide total assurance to customers and internal stakeholders that processes are being improved and upgraded for the highest level of data security.
Improving public image through data protection guarantees
Outside of the practical elements of hard drive degaussing, businesses can also defend their reputation publicly and promote their use of hard drive degaussing as a way to properly handle data. This can strengthen the trust factor for a business with its customer base and also show external stakeholders, governments and organizations that data security is being taken seriously.
Explore our full range of hard drive degaussers and hard disk destroyers and see how you can secure your business data for the future and improve your reputation through transparency and proper data handling. You can also speak to one of our advisors who can provide you with further insight on the hard drive degaussers we provide and what product will be best suited for your organization or business.